In Current COVID-19 outbreak, we probably have to learn some new tools and tricks very quickly now. Here we look at virtual private network (VPN) technology.
‘VPN Services’ is an IT infrastructure management, software consultancy and staff augmentation organization with a vision to provide best-in-class solutions and services in the field of Information Technology.
Hosting Centre provide end-to-end IT services and solutions to help clients leverage leading-edge technologies for business improvement. Based on a match between your business needs and our core competencies, we provide service excellence to our clients. We respond efficiently and effectively to your business challenges through a strategic model that revolves around our core expertise in technologies.
Our extensive technical depth and operational experience are hallmarks of our success. Our Customer Support Engineers are Energetic, Experienced and focused on Total Customer Satisfaction, with a strong dedication towards their work. ‘VPN Services lays great importance on maintaining a vast resource pool, which it taps to provide IT solutions & consulting services to its clients.
For work from home extra online protection from hackers. The software creates a secure connection with another network and then encrypts traffic between those two points.
Global VPN demand rose 41% over last two weeks of March compared to the first half of the month. Even in country like US, we have seen daily demand raised at 65% above the previous average.
From January 2020, approx. 31% of Internet users worldwide use a free or paid VPN. Due to current situation of covid-19, adoption doubled last year to 7% from 3.5% in 2018.
Points to help stay secure when you work from home:
- Keep close contact with your employer
- Use what’s in your company’s tech toolbox
- Avoid 3rd party substitute software to use bridge to main software.
- Stay current on software updates and patches
- Keep your VPN turned on
- Beware of coronavirus-themed phishing emails
- Develop a new routine
Streaming VPN Demand
The following table shows the average increase in daily searches globally for VPN that relate to the leading streaming services.
| Streaming Service | Increase in VPN Demand | +7 Day Demand Increase |
| Disney+ | 154% | 275% |
| Netflix | 90% | 213% |
| HBO | 86% | 100% |
| Amazon Prime Video | 38% | 68% |
| Hulu | 21% | 37% |
| BBC iPlayer | -2% | 4% |
| Grand Total | 85% | 187% |
The benefits of using a VPN
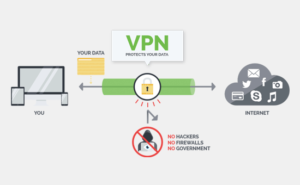
VPN is designed to make internet usage safer, more convenient, and private.
- a) Everything between you and the service or site you are using is encrypted.
- b) A VPN disguises where you are. You may be using your laptop in your city, but the website has no idea where you are.
- c) Defying the trackers “geo-blocking” allows you to see web sites that your location/country prevents you from viewing.
Two common VPN technologies are as follows:
- a) OpenVPNOpenVPN is the software that makes it all possible. OpenVPN’s purpose is simple; it allows you to connect to other devices within one secure network. VPNs secure your online data by tunneling them through encrypted servers, but if you’re looking to keep that very same information safe, and share it with a few trustworthy people (whether they’re employees or friends or family), OpenVPN allows you to do that.
- b) IPsec
IPsec (Internet Protocol Security) provides protection to Network Data Traffic (Primary Goals of IPsec) in four different ways listed below:
1) Confidentiality: The Data in network traffic must be available only to the intended recipient. In other words, the Data in network traffic MUST NOT be available to anyone else other than the intended recipient. IPsec provides Data Confidentiality to Data by Encrypting it during its journey.
2) Integrity: The Data in network traffic MUST NOT be altered while in network. In other words, the Data which is received by the recipient must be exactly same as the Data sent from the Sender. IPsec (Internet Protocol Security) provides Data Integrity by using Hashing Algorithms.
3) Authentication: Sender and the Recipient MUST PROVE their identity with each other. IPsec provides Authentication services by using Digital Certificates or Pre-Shared keys.
4) Protection against Re-play Attacks: Network Re-play attacks (also called as “man-in-the-middle attacks”) allows an attacker to spy the network traffic between a sending device and a receiving device. Later, the Re-play attacker uses the information he gained illegally for fake authentication, fake authorization or to duplicate a transaction. IPsec protects against Re-play attack by using sequence of numbers which are built into the IPsec packets. By using this sequence numbers, IPsec can identify the packets which it has already seen.


No Comments